ZINAD CTF - Reverse
French Man : Easy
This challenge depends on your knowledge about the cipher algo : Vigenère cipher.
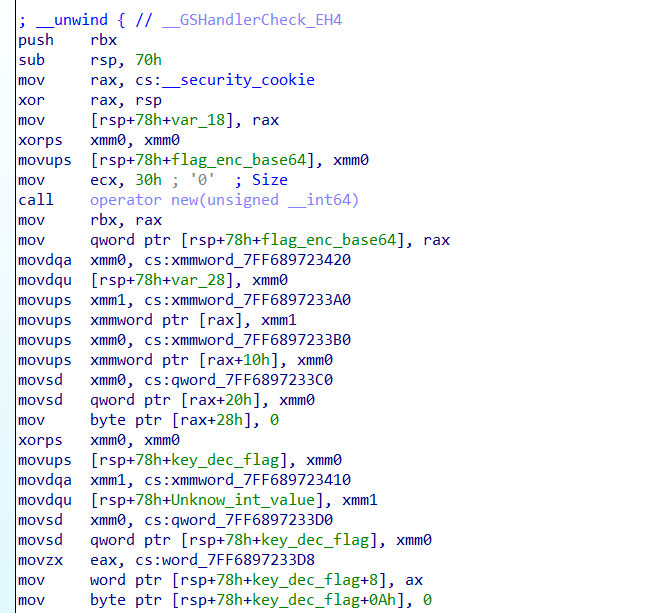
it first loads some values and assign it to a variable:
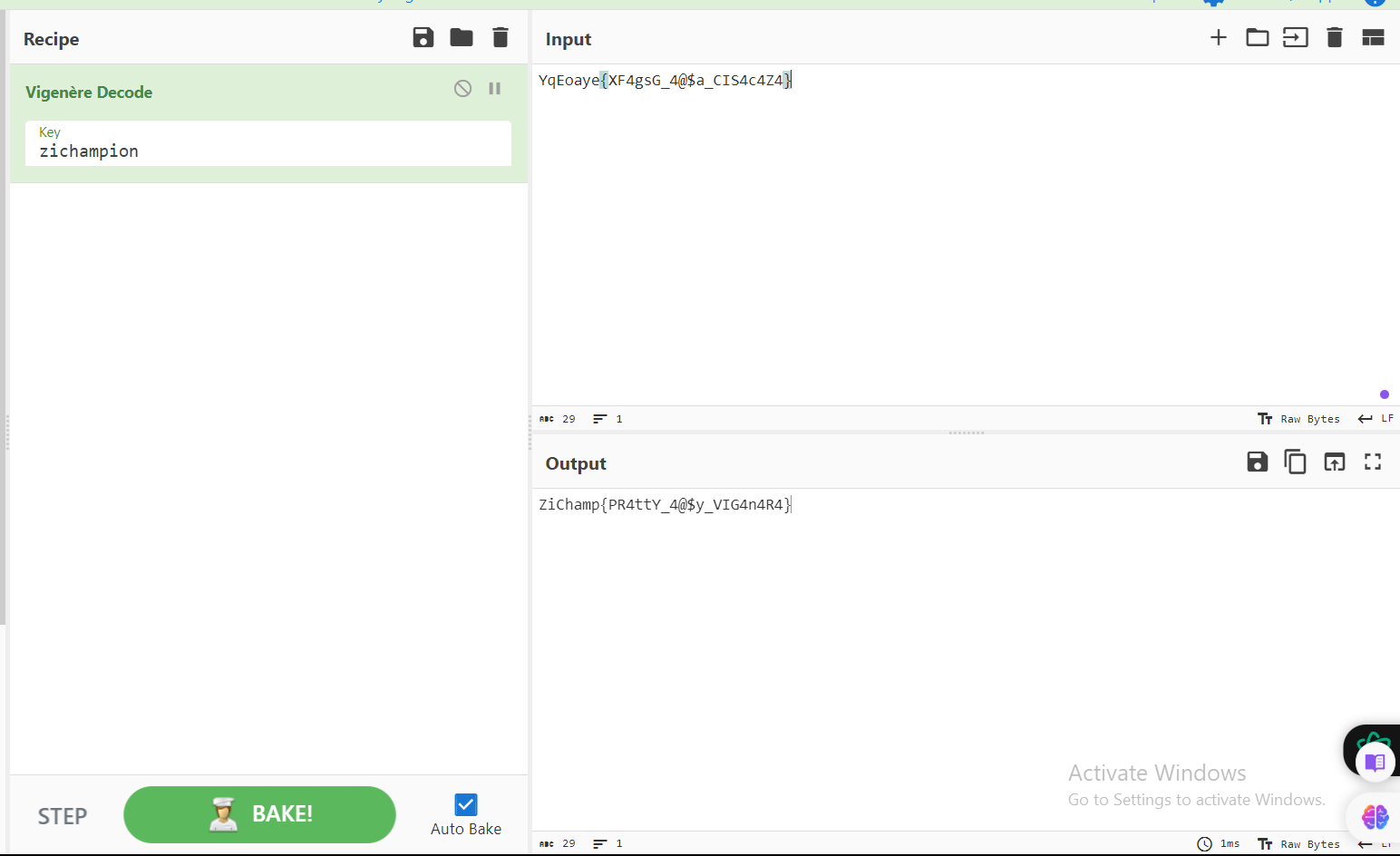
you can notice that it seems to be a base64 encoded string. after decrypting it using any kind of tool it will get you to this : YqEoaye{XF4gsG_4@$a_CIS4c4Z4}.
this string sound interesting, it’s in a form of flag but the characters it self is wrong (the format should be ZiChamp{}).
if you watched the variable you will notice that the program is not going to use it ever. and the app prints some kind of hint: “Do you know the french man?”
so we have a string that’s encoded, and a hint about a french man or something. So it seems to be encoded using Vigenère cipher. Also you may notice that there’s another string that’s stored to another variable and also it won’t used : zichampion, It may be the key for our cipher algo.
using cyberchef, you can now extract the flag :
Secrets Safe : Easy
If we run the program, it seems to be a simple password checker. it asks for a password and if it wrong it ask again for 3 times, then close. when we load it to IDA.
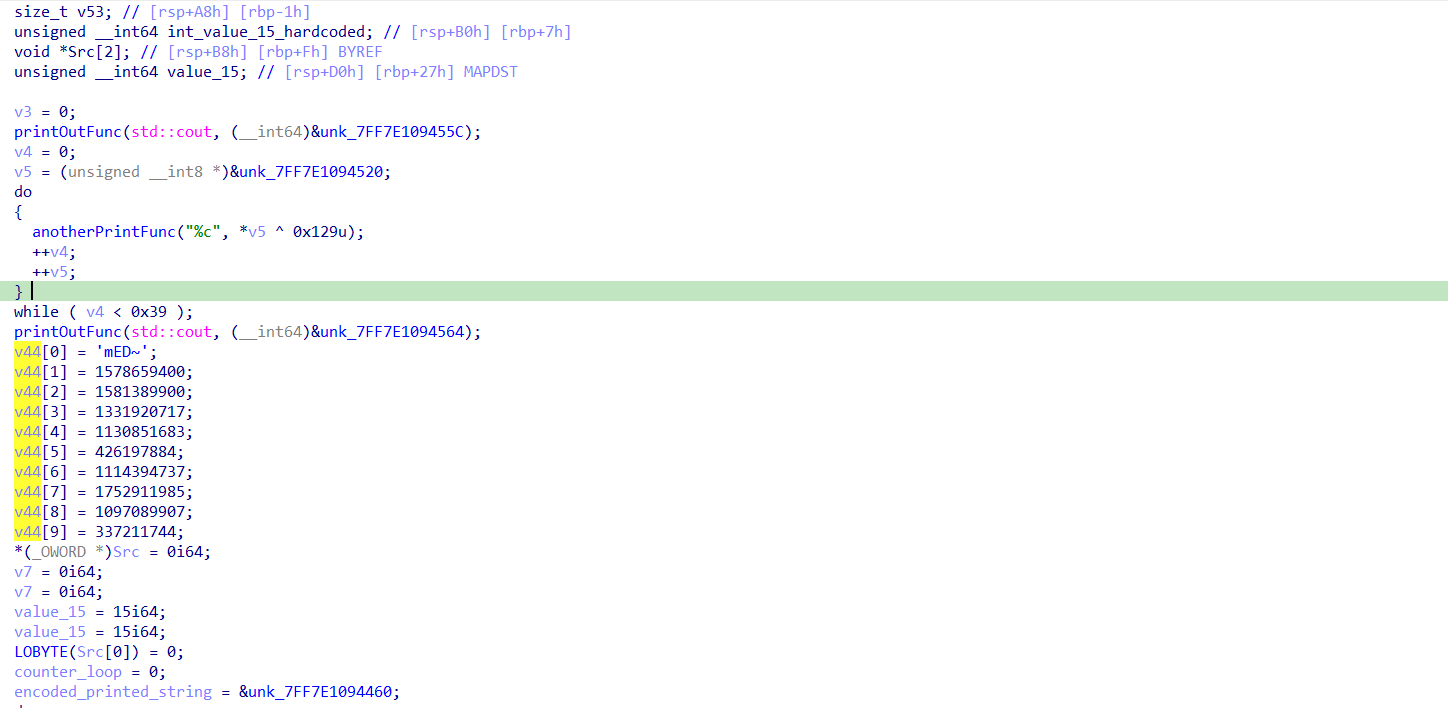
it first initialize some variables, then print out some string then do some decode to another string with XORing it with 0x129 then print it to; from dynamic analysis it’s just the welcome messages when the app firstly run, then it initialize some array with random values, this array looks interesting..
after so it enters another loop that also decode some string using XOR and call function, after analyzing it; it seems to be some function to put some value inside Src pointer And do some string security check and so. if we examine the src pointer we will find that it points to a base64 encoded value (UGxlYXNlIEdpdmUgbWUgdGhlIHNlY3JldCwgSSdtIGEgR29vZCBCb3kuLi4uLi4ucGxlYXNlLCBwbGVhc2UsIHBsZWFzZSEhISE=) , if we decode it : Please Give me the secret, I'm a Good Boy.......please, please, please!!!!. interesting string, we will get back into it later ..
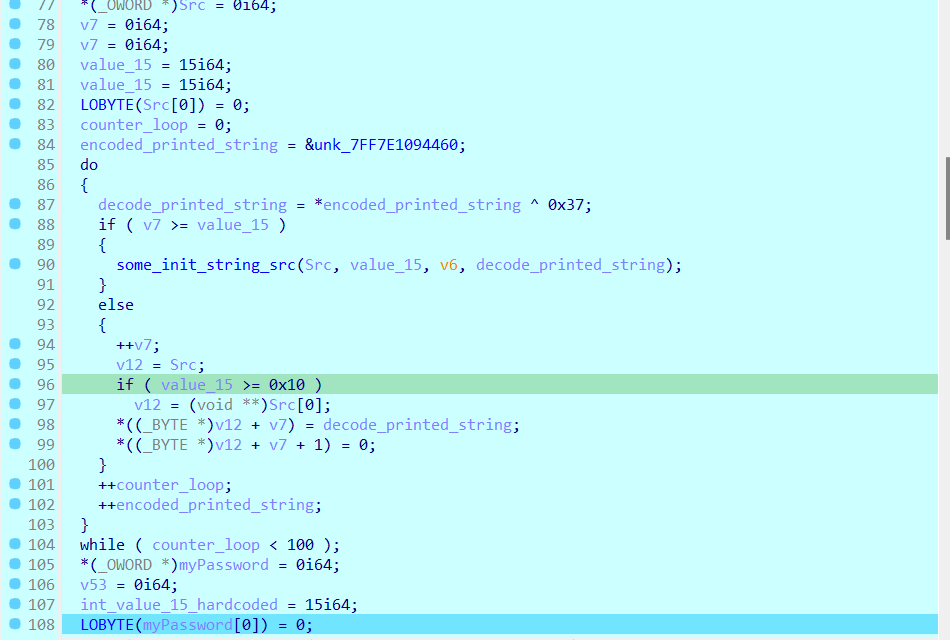
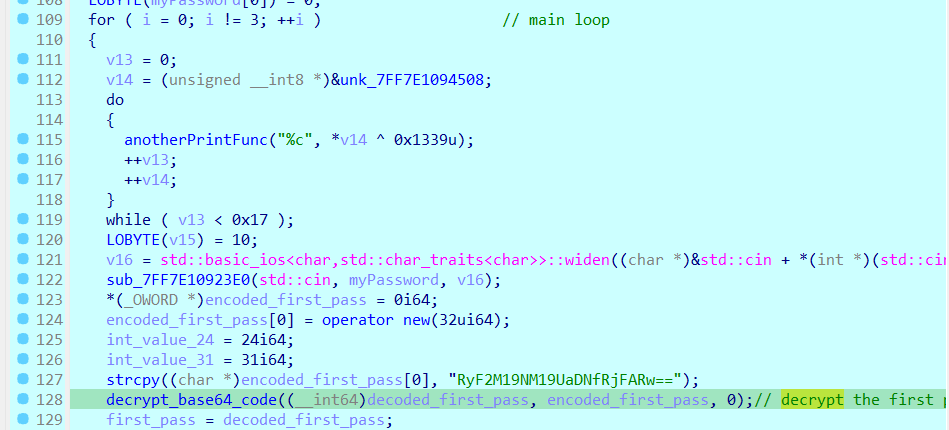
then gets to the main loop (it will repeat three times). from this loop it should firstly print the message that asks for the password (this message is XORed by 0x1339) and waits for my input
then it copies some value that encoded with base64, and after decoding it : G!v3_M3_Th3_F1@G.
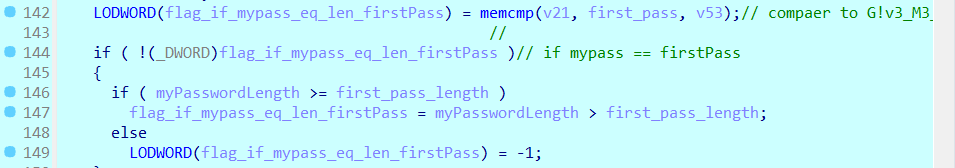
then it do some related string security buffer check and so (compiler generated code, I’m going to ignore it for the rest of the code), after that it check the length of my input and the decoded message, and choose the lowest length and compare between the two strings (my input and the decoded password) using memcmp and set some flag . if my input and the decoded string is equal, then the flag going to be 1 (if the length of my input is bigger) or 0 if they are equal, or finally = -1 if my length is less.
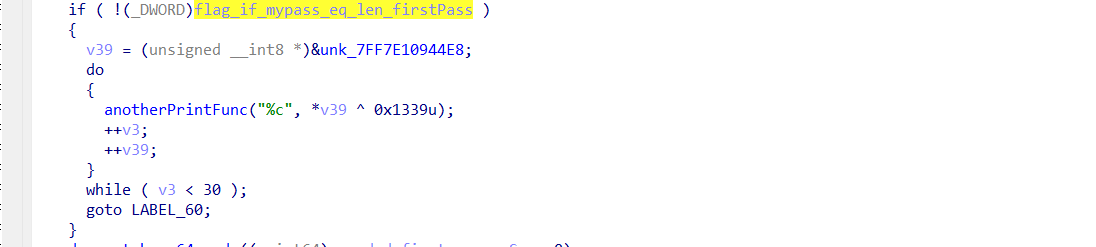
and according to the flag, if it equals to 0; it will decode some message and print it then exit (the message is Life is HARD, so Try HARDER :)):
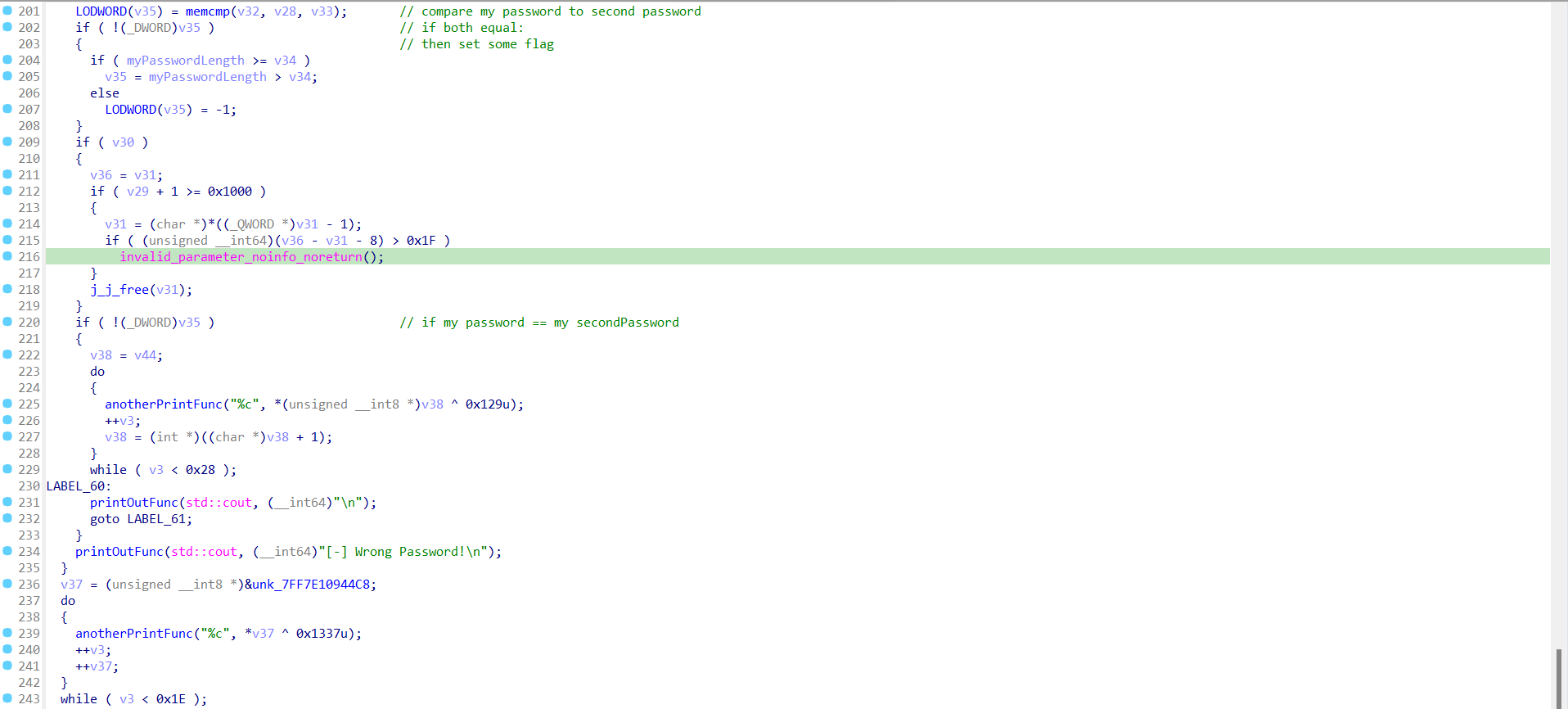
otherwise, it going to decode the value insidesrc pointer as we mentioned before that it has a encoded base64 data. and compare between it and my input (in the same way it did before).
and if they are not equal it will print to you the message [-] Wrong Password!. but if they are equal, it will decode the first array mentioned early by XORing it with 0x129 then exit.
so this is our target, to put the password = Please Give me the secret, I'm a Good Boy.......please, please, please!!!! then it will print to us the password, or get the value inside that array and decode it with XORing each value with 0x129. after you did any the final message will be WmlDaG1we1kwdVJfJDNjUjN0XyEkXyRAZjMhIX0=, after decoding it base64 you will see the flag: ZiChmp{Y0uR_$3cR3t_!$_$@f3!!}.
Medusa : Medium
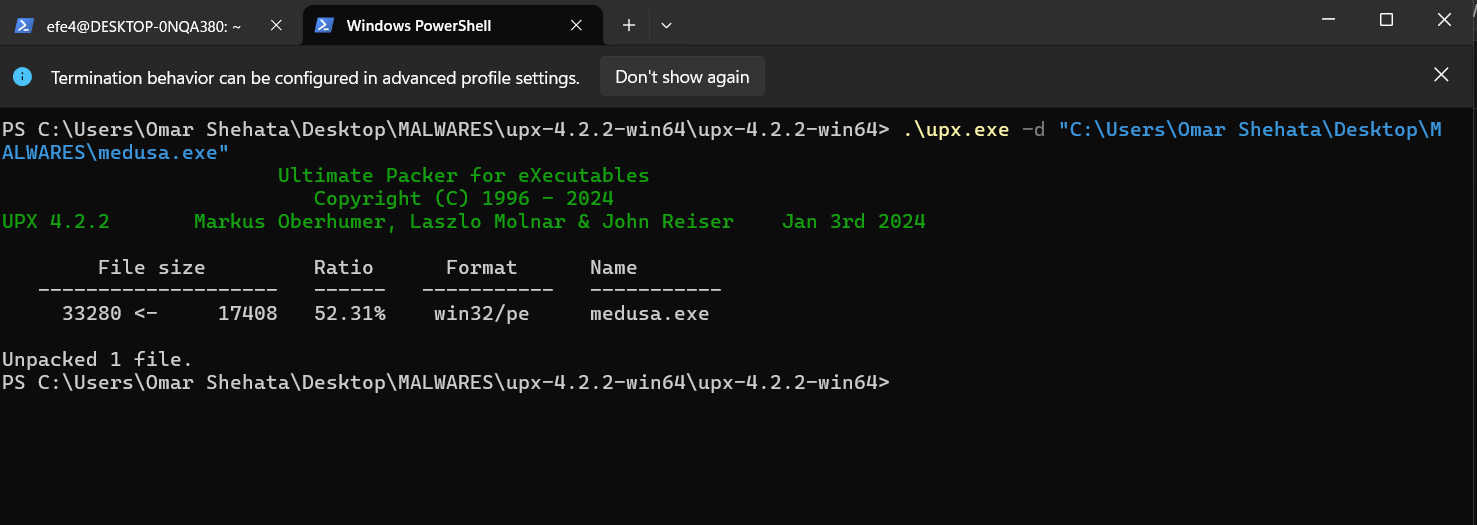
Let’s first examine the PE header. when we do so we will find that it has big entropy and weird section names. so it’s a big indicator that the file is packed, and from any PEHeader analyzer you will know that it’s packed with UPX.
it’s a common packing algorithm, we can unpack it using UPX app, but before this, we should change the section names, because it’s named TPX and this will cause error while unpacking it using UPX app. so changing it to it’s original section names (UPX1, UPX2)(using PE-bear) and then unpack it using the unpacker:
now we have the unpacked version, let’s now try to analyze it using IDA. when we load it we will firstly see that it checks for the IsDebugged bit to know if it’s running under a debugger or not (it’s a common anti-debugging technique) and if the bit is set (meaning the app is being debugged) it will decrypt some message and print it then exit, when we test this message : I Konw what you are doing, and will not let you do it... see you later :)))))))).
we can simply avoid it by changing the value fo ZF from ELFAGS register, or change the bit from memory.
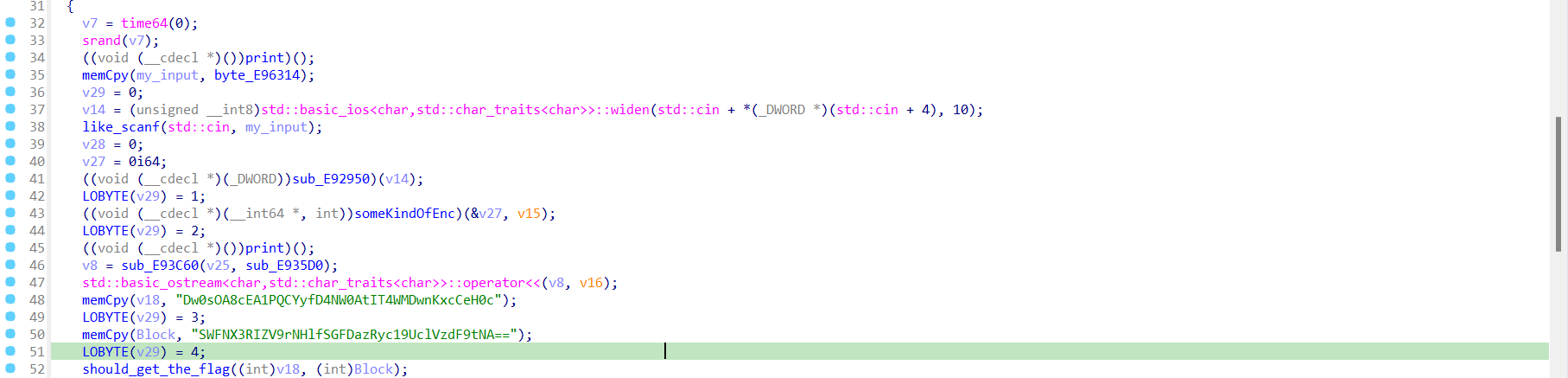
after so it asks for my input, and when I enter it it calls a function to encode it to base64 and print the result. and it will never use my input again !
then it will get two strings seems to be encoded with base64, then pass every string to a function with another pointer, after analyzing it it seems to be a simple memcpy function, it allocate a space that the first pointer will point at then copy the content of the encoded string and put a pointer to that string into the first pointer (so it’s a pointer to pointer). it will do the same for both encoded strings.
then after so it will pass both pointers into our target function. After analyzing this function it seems to be a simple decoder function. it first loads both strings and decode them (from it’s base64 encoding form), and after so it enters a loop to XOR them and store the result into a variable, and then it tries to access an invalid address to cause an exception, but now we got the idea.
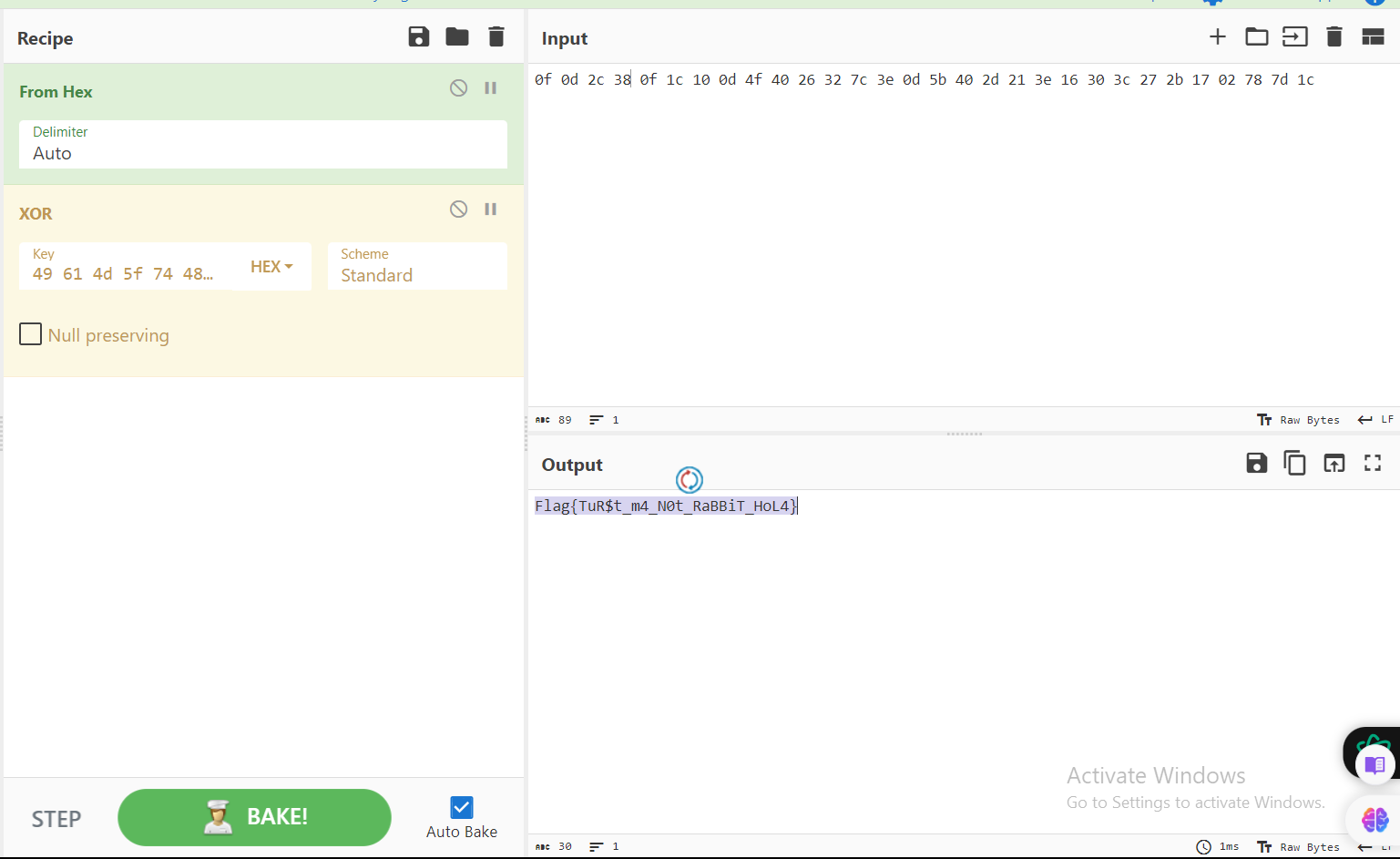
so we need to decode the two encoded strings and XOR them together to get the flag.
the first string is :
Dw0sOA8cEA1PQCYyfD4NW0AtIT4WMDwnKxcCeH0csecond string:
SWFNX3RIZV9rNHlfSGFDazRyc19UclVzdF9tNA==
after decode them with base64 and XOR the result we got the flag: Flag{TuR$t_m4_N0t_RaBBiT_HoL4}
AND THAT’S ALL
thanks for reading.